35+ intrusion prevention system diagram
Create models that illustrate how organisms and their habitats make up a system in which the parts depend on each other. More and more users and businesses use smartphones to communicate.

Ids Vs Ips A Comprehensive Guide To Network Security Solutions
Take the alphanumeric code at end of the broken hyperlink and add to the end of the link.
. For details see the table below the diagram. Soil to milk transfer factor TF dairy daykg milk. The following diagram shows the default ports in a Workload Security system.
Take the accession number and add to the end of the link below. Study with Quizlet and memorize flashcards containing terms like what cryptographic tool is commonly built into a motherboard the facilities manager wants to deploy iot devices for building automation by using an open wireless IEEE based standard. Study with Quizlet and memorize flashcards containing terms like Which Open Systems Interconnection OSI layer assumes responsibility for managing network connections between applications A laptop connects to a web server on the Internet and the service provider then assigns the laptop an IP Internet Protocol address.
These exercises are imperative to understanding issues with an organizations network vulnerabilities and other. For example assume you want your system to boot off a MicroSD card with U-Boot written directly at the beginning of the card followed by a FAT32 partition containing your kernel and device tree and an ext4 root filesystem partition. Instead it furnishes a criticism or comparison that compares the state and behavior of the product against test oracles principles or.
Enters a healthcare systems computer network through software vulnerabilities encrypted traffic downloads and phishing attacks. Which of the following should you recommend an organization chooses among other competing options to replace insecure. Electronic healthcare record process diagram.
TF beef is determined by the following equation for chemicals 25 x 10-8 K ow taken from McKone 1994. Similarly the web server to which the. To fix an outdated citation hyperlink.
Secure your network with an intrusion detection system. But the build system default configurations go a step further and integrate all these pieces together. With up to 64 cores per processor and support for the new PCIe 40 standard for IO the SR665 offers the ultimate in two-socket server performance in a 2U form factor.
Enter the email address you signed up with and well email you a reset link. Categorize resources in various habitats as basic materials eg sunlight air freshwater soil produced materials eg food fuel shelter or as nonmaterial eg safety instinct nature-learned behaviors. Although software testing can determine the correctness of software under the assumption of some specific hypotheses see the hierarchy of testing difficulty below testing cannot identify all the failures within the software.
Circumvent Intrusion detection systems IDS Intrusion prevention systems IPS honeypots and firewalls. TF dairy is determined by the following equation 79 x 10-9 K ow taken from McKone 1994Values for metals come from BAES IAEA NCRP and OTHER. Chapter 10 provides the general criteria for designing the means of egress established as the primary method for protection of people in buildings by allowing timely relocation or evacuation of building occupants.
An exhaust system supply system or combination thereof that is designed to mechanically exchange indoor air for outdoor air where operating continuously or through a programmed intermittent schedule to satisfy the whole-house ventilation rate. The easiest way to remain secure is to. 35 percent of the intrusion operations include hackers conducting MITM exploits as per the IBM X-Force s Threat Intelligence 2018 Reports.
Mobile security or mobile device security is the protection of smartphones tablets and laptops from threats associated with wireless computing. Market is at 236 billion in 2020and AWS is the topmost cloud computing player with a 43 yearly growthThe cloud system infrastructure services. It has become increasingly important in mobile computingThe security of personal and business information now stored on smartphones is of particular concern.
Network administrators should be using good network hygiene to mitigate a man-in-the-middle attack. Soil to beef transfer factor TF beef daykg beef. Top 35 High Paying Business Certifications IT Certifications of 2021-22.
Enter the email address you signed up with and well email you a reset link. To find a specific citation by accession number. Welcome to the IBM Community Together we can connect via forums blogs files and face-to-face networking.
The provisions of this chapter shall control the design construction and arrangement of means of egress components required to provide an approved means of egress from structures and portions thereof. For definition applicable in Chapter 11 see Section N11016 RB WINDBORNE DEBRIS REGION. Sections 1003 through 1030 shall apply to new.
This product guide provides essential pre-sales. Both prescriptive and performance language is utilized in this chapter to provide for a basic approach in the determination of a. Buildings or portions thereof shall be provided with a means of egress system as required by this chapter.
The Lenovo ThinkSystem SR665 is a 2-socket 2U server that features the AMD EPYC 7002 Rome and AMD EPYC 7003 Milan families of processors.
2

Cloud Security With Palo Alto Networks On Oci Oracle Oracle United Arab Emirates
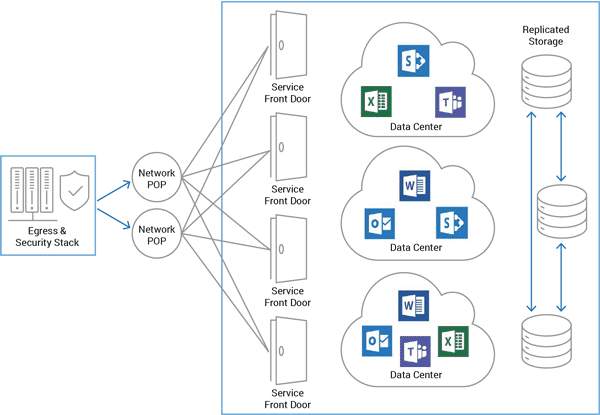
Microsoft Office 365 Enterprise Network Architecture A10 Networks

What Is An Intrusion Detection System And The Types Of It Detection System Id Software

Basics Of Intrusion Detection System Classifactions And Advantages System Detection Electronics Basics
2

A Brief History Of Networking Aiops Blogs Ennetix
2

Probemanager Centralize Management Of Intrusion Detection System Like Suricata Bro Ossec Software Development Hobby Shops Near Me Detection

Ids Vs Ips A Comprehensive Guide To Network Security Solutions

8 Ids And Ips Tools For Better Network Insights And Security Geekflare
2

8 Ids And Ips Tools For Better Network Insights And Security Geekflare

Types Of Ids Behavioral Analysis Content Analysis Analysis
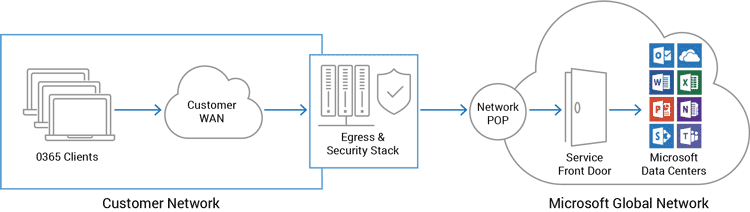
Microsoft Office 365 Enterprise Network Architecture A10 Networks

Computer Security And Pgp What Is Intrusion Detection System Detection Computer Security Network Infrastructure

Ids Vs Ips A Comprehensive Guide To Network Security Solutions